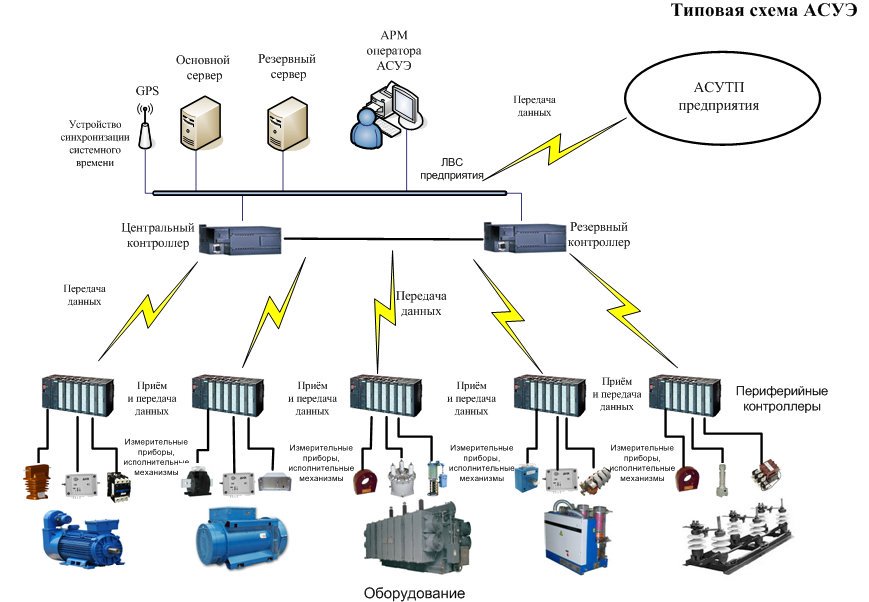
The Secretary of Health and Human Services may impose a civil monetary penalty on any provider of a diagnostic test for COVID-19 that is not in compliance with paragraph (1) and has not completed a corrective action plan to comply with the requirements of such paragraph, in an amount not to exceed $300 per day that the violation is ongoing. In this section, the term in vitro diagnostic test has the meaning given the term in vitro diagnostic product in section 809.3(a) of title 21, Code of Federal Regulations (or successor regulations). Objective or subjective intent that such drug or device be used in a manner inconsistent with any labeling, as applicable, of such drug or device.
- An eligible recipient shall be eligible for forgiveness of indebtedness on a covered 7(a) loan in an amount equal to the cost of maintaining payroll continuity during the covered period.
- Our mission is to close the gaps in opportunity and achievement that disproportionately impact students who are the most underserved, with a particular focus on Black and Latino/a students and students from low-income backgrounds.
- As soon as practicable, but in no case later than 10 days after the date of enactment of this Act, the Secretary shall publish procedures for application and minimum requirements, which may be supplemented by the Secretary in the Secretary’s discretion, for the making of loans and loan guarantees under this section.
- Any emergency financial aid grants to students under this section shall not be treated as other financial assistance for the purposes of section 471 of the Higher Education Act of 1965 (20 U.S.C. 1087kk).
- Not later than 12 months after the date of the enactment of this Act, the Secretary shall convene a public meeting for the purposes of discussing and providing input on improvements to coordination between the Food and Drug Administration and the Centers for Medicare & Medicaid Services in preparing for the availability of novel medical products (as defined in section 1174(b)(2)(B)(iv) of the Social Security Act, as added by subsection (a)) on the market in the United States.
- Not later than 180 days after the date of enactment of this Act, and every 180 days thereafter during the period beginning on the first day of the qualifying emergency and ending on September 30 of the fiscal year following the end of the qualifying emergency, the Secretary shall submit to the authorizing committees (as defined in section 103 of the Higher Education Act of 1965 (20 U.S.C. 1003)) a report that identifies each institution that received assistance or a waiver under this section.
- In conducting the evaluation under paragraph (1), the Comptroller General shall consider, as applicable and appropriate, information from the evaluations under subsection (e)(2)(B).
The Coronavirus Aid, Relief, and Economic Security (CARES) Act (S. Education Fact Sheet
The extent to which such Federal programs are coordinated across agencies and the identification of opportunities for improved coordination in such Federal programs and activities. In conducting the evaluation under paragraph (1), the Comptroller General shall consider, as applicable and appropriate, information from the evaluations under subsection (e)(2)(B). Not later than 4 years after the date of the enactment of this subsection, the Comptroller General of the United States shall conduct an independent evaluation, and submit to the appropriate Committees of Congress a report, concerning Certified Public Accountant the Healthy Start program under this section. In this section, the terms Assistant Secretary, Secretary, State agency, and area agency on aging have the meanings given the terms in section 102 of the Older Americans Act of 1965 (42 U.S.C. 3002). Programs creating records referred to in section 543(a) of the Public Health Service Act (42 U.S.C. 290dd–2(a)) should receive positive incentives for discussing with their patients the benefits to consenting to share such records.
State Stabilization Fund for K-12 and Higher Education
Notwithstanding any other provision of law, the payment for 50 percent of the taxes imposed under section 1401(a) of the Internal Revenue Code of 1986 for the payroll tax deferral period shall not be due before the applicable date. Who experiences adverse financial consequences as a result of being quarantined, being furloughed or laid off or having work hours reduced due to such virus or disease, being unable to work due to lack of child care due to such virus or disease, closing or reducing hours of a business owned or operated by the individual due to such virus or disease, or other factors as determined by Coffee Shop Accounting the Secretary of the Treasury (or the Secretary’s delegate). If a distribution to an individual would (without regard to subparagraph (A)) be a coronavirus-related distribution, a plan shall not be treated as violating any requirement of the Internal Revenue Code of 1986 merely because the plan treats such distribution as a coronavirus-related distribution, unless the aggregate amount of such distributions from all plans maintained by the employer (and any member of any controlled group which includes the employer) to such individual exceeds $100,000. No later than 15 days after enactment of this Act, the Secretary of the Treasury shall submit a plan to the Committees on Appropriations of the House of Representatives and the Senate detailing the expected use of the funds provided by paragraph (1)(A). Beginning 90 days after enactment of this Act, the Secretary of the Treasury shall submit a quarterly report to the Committees on Appropriations of the House of Representatives and the Senate detailing the actual expenditure of funds provided by paragraph (1)(A) and the expected expenditure of such funds in the subsequent quarter.
Terms and settings
The Secretary may choose not to make information collected under this section publicly available pursuant to this section if the Secretary determines that disclosure of such information would adversely affect the public health, such as by increasing the possibility of unnecessary over purchase of product or other disruption of the availability of medical products to patients. In carrying out this subsection with respect to any establishment manufacturing a drug approved under subsection (c) or (j) of section 505 for which a notification has been submitted in accordance with section 506C is, or has been in the last 5 years, listed on the drug shortage list under section 506E, or that is described in section 505(j)(11)(A), a copy of the report shall be sent promptly to the appropriate offices of the Food and Drug Administration with expertise regarding drug shortages. Such offices shall ensure timely and effective coordination regarding the reviews of such report and overseeing the alignment of any feedback regarding such report, or corrective or preventative actions, after consideration of the systematic benefits and risks to public health, patient safety, the drug supply and drug supply chain, and timely patient access to such drugs. A United States business that has incurred covered losses such that the continued operations of the business are jeopardized, as determined by the Secretary, and that has not otherwise applied for or received economic relief in the form of loans or loan guarantees provided under any other provision of this Act. Amounts collected from eligible businesses that received loans or loan guarantees under paragraph (3) of subsection (b) shall be deposited in the Treasury as miscellaneous receipts.

To facilitate implementation of subparts 1 and 2 of part C of title III of the Older Americans Act of 1965 (42 U.S.C. 3030d–2 et seq.) during any portion of the COVID-19 public health emergency declared under section 319 of the Public Health Service Act (42 U.S.C. 247d), the Assistant Secretary shall waive the requirements for meals provided under those subparts to comply with the requirements of clauses (i) and (ii) of section 339(2)(A) of such Act (42 U.S.C. 3030g–21(2)(A)). The health care professional rendered the health care services under the influence (as determined pursuant to applicable State law) of alcohol or an intoxicating drug. For the time in which the public health emergency under section 319 of the Public Health Service Act (42 U.S.C. 247d) related to the coronavirus (COVID-19), declared by the Secretary of Health and Human Services (referred to in this section as the Secretary) on January 31, 2020, is in place (or such other period of time determined by the Secretary), tests intended to diagnose COVID–19 that are described in subsection (b) may be lawfully marketed in accordance with this section.
- Qualified family leave wages for which a credit is allowed under section 7003 of the Families First Coronavirus Response Act.
- For purposes of paragraph (1), the term valid identification number means a social security number (as such term is defined in section 24(h)(7)).
- Canceled indebtedness under this section shall be excluded from gross income for purposes of the Internal Revenue Code of 1986.
- The term coronavirus means coronavirus as defined in section 506 of the Coronavirus Preparedness and Response Supplemental Appropriations Act, 2020 (Public Law 116–123).
- Has an application for a loan made under section 7(a) of the Small Business Act (15 U.S.C. 636(a)) that is approved or pending approval on or after the date of enactment of this Act.
In the case of an individual, the due date for any required installment under section 6654 of the Internal Revenue Code of 1986 which (but for the application of this section) would be due during the applicable period shall not be due before October 15, 2020, and all such installments shall be treated as one installment due on such date. The Secretary of the Treasury (or the Secretary’s delegate) shall prescribe such regulations or other guidance as may be necessary to carry out the purposes of this subsection. The Agency may provide financial assistance in the form of grants to minority business centers to provide education, training, and advising to covered small business concerns.

Any provision of a loan agreement or insurance agreement modified or waived by the authority under this section shall remain so modified or waived for the duration of the period covered by the loan agreement or insurance agreement. Except as provided in paragraph (B), a waiver approved by the Secretary of Education under this subsection may be for a period not to exceed 1 academic year. The description required under paragraph (2)(C) provides insufficient information to demonstrate that the waiving of such requirements is necessary or appropriate consistent with subsection (a).
Should Congress pass this $1 trillion economic relief bill during the coronavirus outbreak?

For purposes of paragraph (1)(C), in the case of a qualifying child who is adopted, the term valid identification number shall include the adoption taxpayer identification number of such child. In the case of a refund or credit made or allowed under subsection (g) with respect to a joint return, half of such refund or credit shall be treated as having been made or allowed to each individual filing such cares act s.3548 return. Under the infrastructure of the Department of the Treasury and with guidance from the Secretary of the Treasury, the Administration shall administer the program established under this section until the date on which the national emergency declared by the President under the National Emergencies Act (50 U.S.C. 1601 et seq.) with respect to the Coronavirus Disease 2019 (COVID–19) expires. Not later than 180 days after the date of enactment of this Act, the Administrator shall submit to the Committee on Appropriations of the Senate and the Committee on Appropriations of the House of Representatives a detailed expenditure plan for using the amounts appropriated under subsection (a).
- For purposes of paragraph (19) of subsection (a), the terms Military department, Secretary concerned, and Armed forces in such title 10 shall be deemed to include, respectively, the Department of Health and Human Services, the Secretary of Health and Human Services, and the Commissioned Corps.
- The sponsor of a new animal drug may request the Secretary to designate a new animal drug described in subsection (a) as a priority zoonotic animal drug.
- A net operating loss for a REIT year shall not be a net operating loss carryback to any taxable year preceding the taxable year of such loss.
- The term direct primary care service arrangement means, with respect to any individual, an arrangement under which such individual is provided medical care (as defined in section 213(d)) consisting solely of primary care services provided by primary care practitioners (as defined in section 1833(x)(2)(A) of the Social Security Act, determined without regard to clause (ii) thereof), if the sole compensation for such care is a fixed periodic fee.
- No additional payment shall be made under subparagraph (K) for discharges involving a DISARM antimicrobial drug as a new medical service or technology if any additional payments for discharges involving such drug have been made under this subparagraph.
S. 3548 (116th) was a bill in the United States Congress.
The amendments made by this section shall apply to months beginning after December 31, 2019, in taxable years ending after such date. In the case of a direct primary care service arrangement (as defined in section 223(c)(1)(D)(ii)) which is provided in connection with employment, the aggregate fees for such arrangement for such employee. For purposes of this section and section 105, expenses incurred for menstrual care products (as defined in section 223(d)(2)(D)) shall be treated as incurred for medical care.